Steps
To configure Agentless User-ID, first create the service account, then modify and verify security settings.
Configure the following on the Active Directory (AD) Server and the Palo Alto Networks device:
- Create the service account in AD, which is utilized on the device. Be sure the user is part of the following groups:
- Distributed COM Users
- Event Log Readers
- Server Operators
Note: Domain Admin privileges are not required for the User-ID service account to function properly, see Best Practices for Securing User-ID Deployments for more information.
In Windows 2003, the service account must be given the “Audit and manage security log” user right through a group policy. Making the account a member of the Domain Administrators group provides rights for all operations. The built-in group named “Event Log Readers” is not available in Windows 2003. - The device uses WMI Authentication and the user must modify the CIMV2 security properties on the AD server that connects to the device.
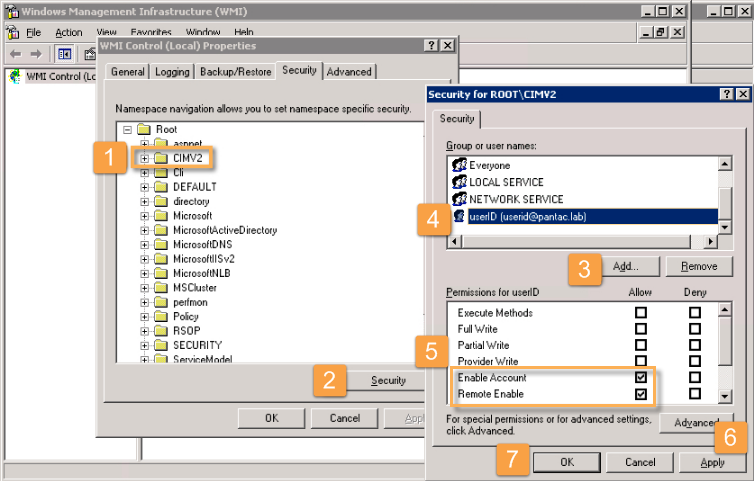
- Run 'wmimgmt.msc' on the command prompt to open the console and select these properties:
- From the Security tab on WMI Control Properties:
1.) Select the CIMV2 folder.
2.) Click Security,
3.) Click Add and then select the service account from Step 1.
4.) In this case, it is userid@pantac.lab.
5.) For this account, check both Allow for Enable Account and Remote Enable:
6.) Click Apply,
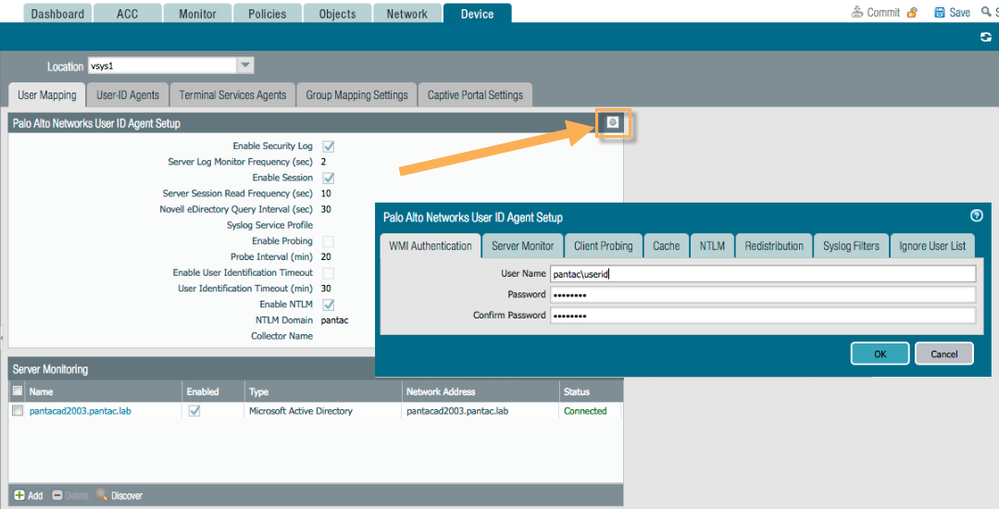
7.) Then click OK. - Back in the Palo Alto WebGUI, Select Device > User Identification > User Mapping, then click the edit sproket in the upper right corner to complete the Palo Alto Networks User-ID Agent Setup.
- Be sure to configure with the domain\username format for username under WMI Authentication tab along with valid credentials for that user.
- Enable the Server Monitor options and enable the security log/enable session accordingly.
Client probing is enabled by default, so disable if desired. - If the domain is configured during Setup in the General Settings/Domain field, the user can elect to discover servers with which to connect. If not, manually add a server to the device:
- Confirm connectivity through the WebGUI or the CLI:
> show user server-monitor statistics Directory Servers: Name TYPE Host Vsys Status ----------------------------------------------------------------------------- pantacad2003.pantac.lab AD pantacad2003.pantac.lab vsys1 Connected
- Confirm that ip-user-mapping is working.
> show user ip-user-mapping all IP Vsys From User IdleTimeout(s) MaxTimeout(s)--------------- ------ ------- -------------------------------- -------------- ----------192.168.28.15 vsys1 AD pantac\tom 2576 2541192.168.29.106 vsys1 AD pantac\userid 2660 2624192.168.29.110 vsys1 AD pantac\userid 2675 2638Total: 3 users
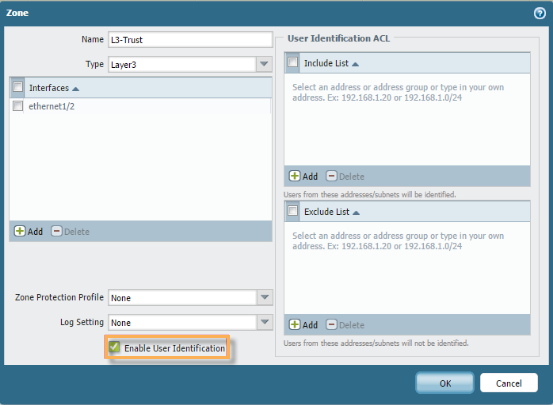
- Ensure Enable User Identification is enabled on the zones where identifiable traffic will be initiated. Select the zone in Network > Zone.





No comments:
Post a Comment