Objectives Of 15-Steps Visual Guide
The ultimate guide to understand the nuances of integrating GNS3 with VMWare WorkStation version 10/11/12. Two approaches of this integration has been elaborated & presented in this visual guide.
The idea is to provide the helping tool to candidates aspiring to practice and obtain their CCIE, CCNP, CCNA certifications.

We will create and configure the above topology. For that we need, two routers (ISP-India, ISP-US), two hosts (LuminisIndia.com, Client), and two Virtual Networks:
- LuminisIndia will use this network 200.200.200.0/24.
- Client will use this network 33.33.33.0/24.
We will achieve the fully working topology as shown above, by following the steps in this Visual Guide created by: Meena, Sr. Manager IT and Consultant. So let's start.
Step 1
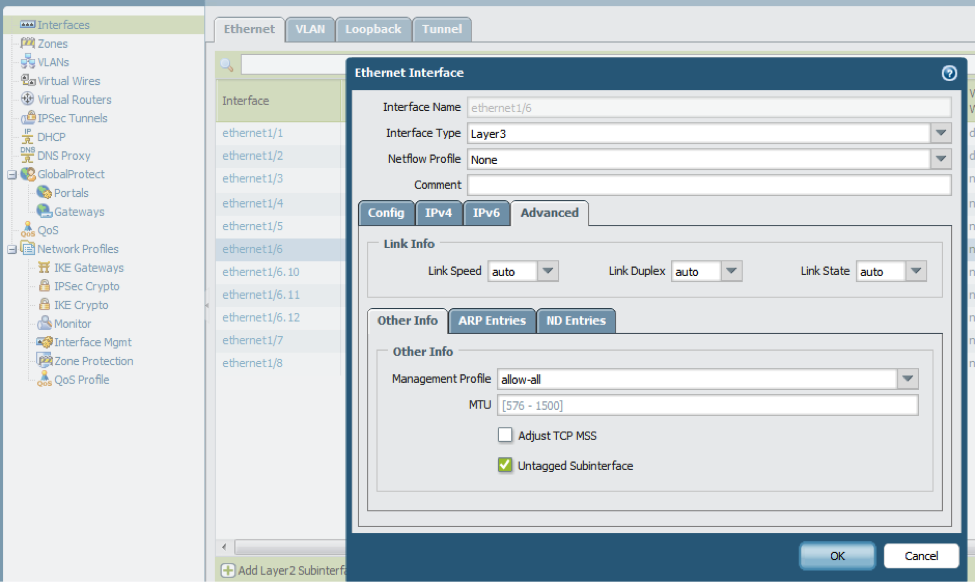
Start your VMware workstation software and open the Virtual Network Editor through Edit menu of VMware. Then click on Change Settings first, so as to allow us creation of Virtual Networks.
Step 2
Now we can add the Virtual Networks. Click on Add Network and select the VMnet (VMnet2) from the drop down list and click on OK.
You can see that a new Virtual Network has appeared VMnet2 in the Virtual Network Editor and it has a default subnet, e.g., 192.168.228.0 with subnet mask 255.255.255.0. But we will not use the given subnet, instead we will change it to 200.200.200.0/24.
If we want to assign IP address automatically to our hosts (PCs or VMs or Servers), we can use the DHCP service which is the part of this Virtual Network. To set the specific range of IP for the host click on DHCP Settings and specify the range of IP.
Step 3
We will follow Step2 again and create the 2nd Virtual Network VMnet3, assign the subnet 33.33.33.0/24 and also change the DHCP Settings.
We can see here are the two new Virtual Networks.
Step 4
Open Network and Sharing Center from your Windows 7/8/10, etc and you will find the two new VMware Network Adapters. Go to VMware Network Adapter VMnet3. Here you can see that DHCP has assigned the IP 33.33.33.1/24 to VMware Network Adapter VMnet3.
But we will assign the IP address 33.33.33.1 as a Default gateway, which will, in effect, become the IP address of ISP-US Router. Now we have choice of assigning any IP address from the range of 33.33.33.2 - 33.33.33.254 , to VMware Network Adapter VMnet3. Here we are choosing 33.33.33.33/24 for the sake of convenience.
Now, we will change the name of VMWareNetwork Adapter VMnet3 to Client.
Step 5
In this step, we will see the status of VMware Network Adapter VMnet2.
We can see that the IP address assigned by the DHCP is 200.200.200.1/24. But we will assign the IP address 200.200.200.1 as a Default gateway, which will, in effect, become the IP address of ISP-India Router. Now we have choice of assigning any IP address from the range of 200.200.200.2 - 200.200.200.254 , to VMware Network Adapter VMnet2. Here we are choosing 200.200.200.200/24 for the sake of convenience.
Then change the name of VMware Network Adapter VMnet2 to LuminisIndia.
Step 6
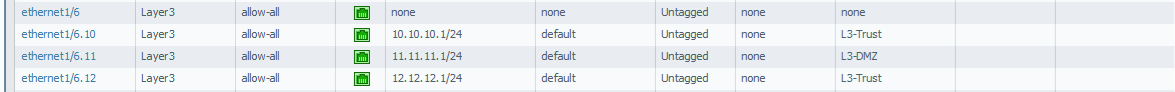
Start your GNS3 and create the topology of the network which we will use. Drag the two routers and two hosts. Then change the name of these to : R1 (ISP-India), R2(ISP-US), Host1 (LuminisIndia.com), Host2 (Client).
Add the notes for network addresses and IP addresses which we will use in this topology.
Step 7
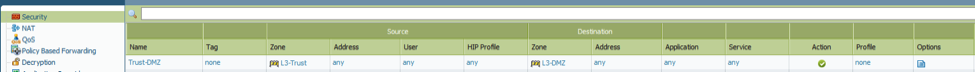
Link the VMware Network Adapters with the Hosts, e.g. Host LuminisIndia.com with LuminisIndia (VMware Network Adapter VMnet2), Host Client with Client (VMware Network Adapter VMnet3).
Sometimes the newly created VMware Network Adapters doesn't appear in the list. You must save your project of GNS3 and reload it. Then all the Network Apaters will appear. Be careful In this process, because wrong association will create more confusion in the desired results.
Step 8
Now connect the devices and also make a note of the interface number you are going to use in your topology. I always use paper to draw the full topology, means: devices, interfaces no., network addresses, IP addresses, etc. This helps me in configuration and trobleshooting. Then start (power on) all the devices.
Now ensure that your Client and LuminisIndia (VMware Network Adapters) must be enabled and keep the rest of Network Adapters Disabled. This step will help you in verification process.
Step 9
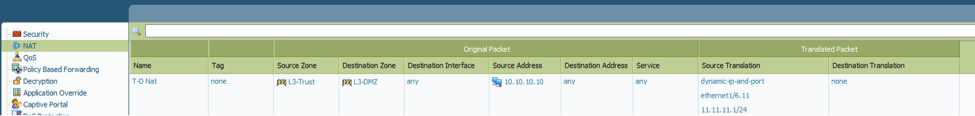
In this step, we will configure the Routers. On router ISP-India, you can see that IP Address on Interface Ethernet 0/0 is 200.200.200.1/24, which is connected with the Host LuminisIndia.com and this IP is the Default Gateway, on VMware Network Adapter LuminisIndia. Assign the IP Address 12.1.1.1/30 to the Interface Serial 1/1. Your intereface no. can be different. For routing, use Routing Protocol EIGRP and advertise the networks 12.0.0.0 and 200.200.200.0.
Also configure the ISP-US router as per the configuration given in the below image.
Step 10
After completing the configuration, next part is the testing or verification. First, try to ping the directly connected devices, if you face any problem troubleshoot it. Then open two command prompts and try to ping both the hosts and routers as well, as I did in the below image. If you get the successful reply, that means you have configured everything properly.
Are you sure that everything is working in the same way we are expecting?
Step 11
Let's take the another approch for verification of our configuration. On the Router ISP-US, SHUTDOWN the interface Ethernet0/0 which is connected with the Client. Try to ping 33.33.33.33 from router and also check the Interface Status, by following the commands of below image.
Try to ping the IP 33.33.33.1 from the command prompt. Now ping 12.1.1.2 which the IP on ISP-US, and then use the tracert command. You can see that the traffic is going through ISP-India to ISP-US. You can also see the results in below image.
In the above results you would have observed that from ISP-US router you cann't ping the host Client and from the command prompt you cann't ping the 33.33.33.1. It means that the interface is down, which is not allowing the ping.
Now run the NO SHUTDOWN command of the interface Ethernet 0/0, this will UP the interface and will allow the traffic to pass through the interface.
The same testing we will do with LuminisIndia, but using a different approach. Now disable the VMware Network Adapter LuminisIndia.
You can follow the testing commands given in the below image. I think with this apporach things will be more clear.
NOTE: With the above steps, you can do your Cisco Labs and you also need not to create the Virtual Machines.
But if you need more services and/or you need the Virtual Machines, then follow the further steps of this visual guide.
Step 12
Start the New Virtual Machine Wizard from the File Menu.
Follow the instructions in the wizard and create the Virtual Machine (VM).
Step 13
Now Edit the VM, select the Operating System image which you want to install on this VM. Associate the VMnet to it, and then Power on the VM. I have given the name LuminisIndia to this VM and VMnet2 (200.200.200.0/24) Virtual Network to this VM.
Step 14
Install the Operating System on the VM, you can see the below image.
Now we will check the status of the Network Adapter of this newly installed VM. You can see that it received the IP Address automatically from the DHCP Local server of this VMnet.
Now, change the IP address and Default gateway as per the image given below and also turn off your windows Firewall or Antivirus.
Step 15
Follow the testing as per below image.
And if you need the another VM, you can follow the above steps.
I hope this will help you understand the Integration of the GNS3 with VMware Workstation.