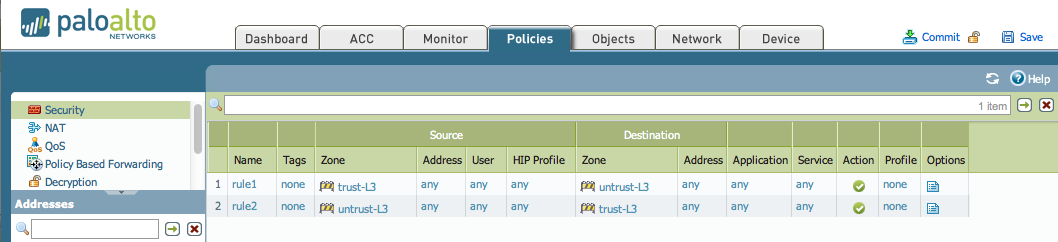
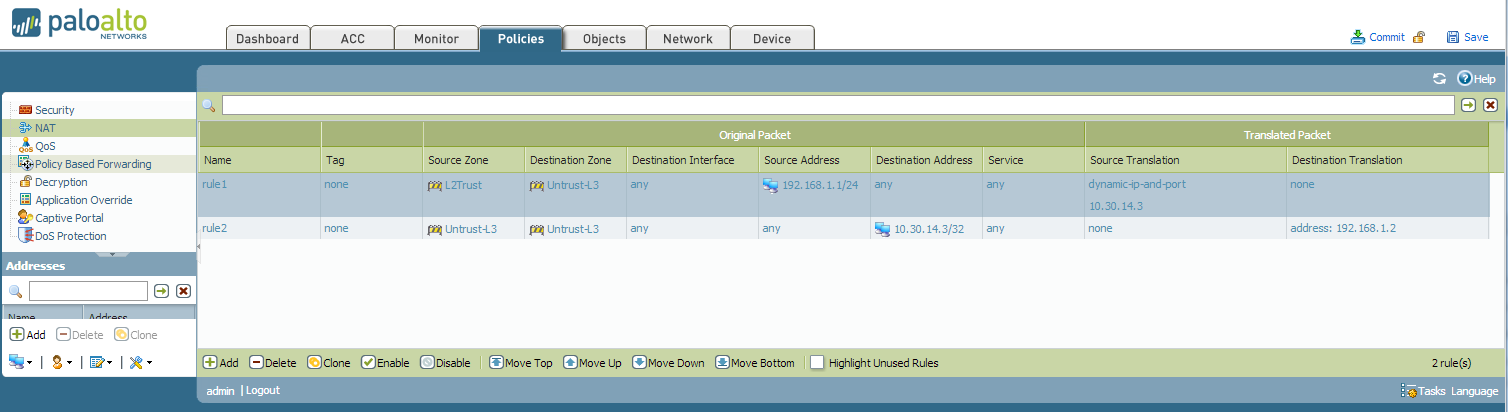
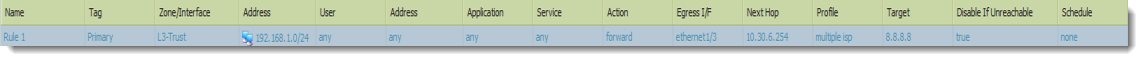
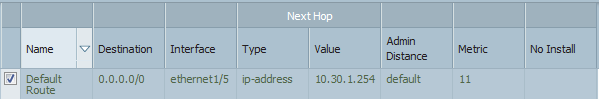
Palo Alto Networks Next-Generation Firewalls rely on the concept of security zones in order to apply security policies. This means that access lists (firewall rules) are applied to zones and not interfaces – this is similar to Cisco’s Zone-Based Firewall supported by IOS routers.
Palo Alto Networks Next-Generation Firewalls zones have no dependency on their physical location and they may reside in any location within the enterprise network. This is also illustrated in the network security diagram below:
The above topology illustrated shows VLANs 10, 11 ,12 and 2 managed by a Cisco Catalyst 4507R+E Switch and are all part of OSPF Area 0 and visible as routes in the Palo Alto Firewall. A Layer 3 aggregated link has been created between the Palo Alto Firewall (Interface ae1 on each firewall) and the Cisco 4507R+E Switch (Port-Channel 1 & 2).
When aggregation interface ae1.2 on the Palo Alto Firewall is configured to be part of the DMZ Security Zone, all networks learnt by the OSPF routing protocol on interface ae1.2 will be part of the DMZ Security Zone.
Creating a Security Zone involves tasks such as naming the zone, assigning the interfaces to the new zone created and more. Palo Alto Networks Next-Generation Firewalls won’t process traffic from any interface unless they are part of a Security Zone.
The diagram below depicts the order in which packets are processed by the Palo Alto Firewall:
It is without doubt Zone based firewalls provide greater flexibility in security design and are also considered easier to administer and maintain especially in large scale network deployments.
Palo Alto Networks Next-Generation Firewalls have four main types of Zones namely as shown in the screenshot below:
- Tap Zone. Used in conjunction with SPAN/RSPAN to monitor traffic.
- Virtual Wire. Also known as Transparent Firewall.
- Layer 2. Used when switching between two or more networks.
- Layer 3. Used when routing between two or more networks. Interfaces must be assigned an IP address.
Figure 3. Types of Security Zones in Palo Alto Firewalls
Palo Alto Networks Next-Generation Firewalls have special zone called External which is used to pass traffic between Virtual Systems (vsys) configured on the same firewall appliance. The External zone type is only available in the Palo Alto Networks Next-Generation Firewalls which are capable of Virtual Systems and also the External Zone is visible only when the multi-vsys feature is enabled.
CREATING A SECURITY ZONE
This section focuses on creating different types of Security zones in Palo Alto Networks Next-Generation Firewalls
Step 1. Login to the WebUI of Palo Alto Networks Next-Generation Firewall
Step 2. From the menu, click Network > Zones > Add
Figure 4. Creating a new Zone in Palo Alto Firewall
Step 3. Provide the name for the new Zone, and select the zone type and click OK:
Figure 5. Creating a zone in a Palo Alto Firewall
In a similar manner we can repeat steps 1 to 3 to create Tap, Virtual Wire or Layer 2 security zones.
Finally it is important to note that the zone names is case sensitive, so one needs to be careful as the zone FiewallCX and firewallcx are considered different zones:
Figure 6. Identically named Security zones using different letter cases result in different Security zones
Figure 7. Example of case sensitive security zones with identical zone names
Creating a security zone in Palo Alto Networks Next-Generation Firewalls involves three steps:
Step 1. Specify the Zone name
Step 2. Select the Zone type
Step 3. Assign the Interface
The interfaces part will be dealt in upcoming posts as one need to understand types of interfaces Palo Alto Networks Next-Generation Firewalls offers and how they work.
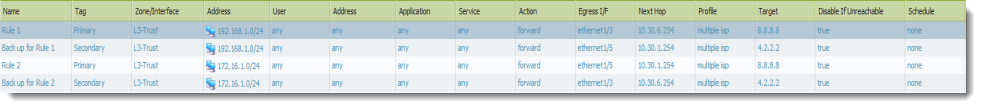
In Palo Alto Networks Next-Generation Firewalls zone names have no predefined meaning or policy associations, basically they are created to group the services by functions for examples one can group all the Domain Controllers in one security group no matter even if they are part of different networks.
Figure 8. Example of grouping Domain Controllers in same security zone – DMZ
As mentioned Palo Alto Networks Next-Generation Firewalls works with the principle of Security zones, by default Intra-Zone traffic is allowed and Inter-Zone traffic is denied. More technical articles can be found in our Palo Alto Network Firewall section.